Chapter 3. System Configuration
One of the main strengths of Red Hat Linux is that the operating system can be configured to do just about anything. In the past, this meant editing sometimes cryptic configuration files by hand, then restarting system services and crossing your fingers in the hope that your changes were correctly made. Additionally, the variety of configuration options can be bewildering to new users, who may not know where to look for a particular configuration file.
Red Hat Linux provides two system configuration utilities: linuxconf and the control panel. The control panel provides a launcher for various Red Hat system configuration tools, including linuxconf. Instructions on how to use the control panel and the tools it includes can be found in the section called System Configuration with the Control Panel.
The linuxconf configuration tool can ease some of the burdens of system configuration. Linuxconf is both:
A configuration interface — You type the values needed to configure your system into a user interface.
A configuration activator — When you're satisfied with your edits, you tell linuxconf to apply the changes you've made.
While linuxconf can do nearly everything the control panel tools can, there are two areas in which the control panel still holds the upper hand:
Printer configuration
Loading kernel modules to support new hardware
Let's take a look at linuxconf.
System Configuration with linuxconf
Linuxconf allows you to configure and control various aspects of your system, and is capable of handling a wide range of programs and tasks. Complete documentation of linuxconf could be a separate book in its own right and is certainly more than we can cover in this chapter. Instead, we'll focus on common tasks such as adding new users and getting connected to a network.
More information on linuxconf, including its most recent release can be found at the linuxconf website:
http://www.solucorp.qc.ca/linuxconf/
The linuxconf website includes fairly extensive information, including a description, rationale, history, list of contacts, and a lot of other information in addition to the software. The website is maintained by linuxconf's creator and developer, Jacques Gelinas, so it includes the latest news about linuxconf.
This chapter will go into detail on just a few of linuxconf's capabilities. If you just need a quick reference to show you where to go in linuxconf for the tasks covered by this chapter, see the section called Finding Your Way Through linuxconf.
If you need more help with linuxconf, please try these sources:
The linuxconf FAQ, which is available at http://www.xc.org/jonathan/linuxconf-faq.html.
The archives of the linuxconf mailing list, which are available at http://hub.xc.org/scripts/lyris.pl?visit=linuxconf.
After you've checked the linuxconf FAQ and the archives of the linuxconf list, you might try posting your question to the linuxconf list. Subscription information for the linuxconf list is available at the linuxconf website (http://www.solucorp.qc.ca/linuxconf/); click on the "Mailing lists" link.
Please note that this list is for questions pertaining to linuxconf, and is not intended for general Linux questions.
Running linuxconf
You'll need to be root to run linuxconf, so if you're in your user account, su to become root.
Now, type linuxconf at the shell prompt to begin the program.
Linuxconf User Interfaces
Linuxconf has four user interfaces:
Text-based — Using the same user interface style as the Red Hat Linux text-mode installation program, the text-based interface makes it easy to navigate your way through linuxconf if you aren't running X. If you are running X, you can switch to a virtual console, log in as root, and type linuxconf to bring up text-mode linuxconf.
Use the Tab and arrow keys to navigate the text-mode screens. A down arrow on a line indicates that a pull-down menu exists on that line. The Ctrl-X key combination will make pull-down menus appear.
Graphical user interface (GUI) — linuxconf can take advantage of the X Window System. Red Hat Linux includes a GUI interface for linuxconf called gnome-linuxconf.
This document will display linuxconf screens using the gnome-linuxconf interface, but you shouldn't have any trouble using the other interfaces with the instructions provided here.
Web-based — A Web-based interface makes remote system administration a breeze; it can also be displayed with the Lynx text-mode browser.
To use the linuxconf Web interface, use your browser to connect to port 98 on the machine running linuxconf (i.e., http://your_machine:98).
Before you use the Web-based interface, you'll need to configure linuxconf to allow connections from the machine running the browser. See the section called Enabling Web-Based linuxconf Access for instructions on enabling Web access to linuxconf.
Command line — linuxconf's command-line mode is handy for manipulating your system's configuration in scripts.
Linuxconf will start in either character-cell or X mode, depending on your DISPLAY environment variable. The first time you run linuxconf, an introductory message will be shown; although it is only displayed once, accessing help from the main screen will give you the same basic information.
Linuxconf includes some context-specific help. For information on any specific aspect of linuxconf, select Help from the screen you'd like help with. Note that not all help screens are complete at this time; as help screens are updated, they will be included in subsequent versions of linuxconf.
gnome-linuxconf Interface
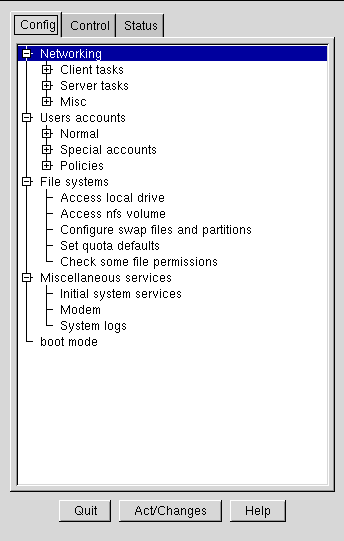
gnome-linuxconf makes it easy to navigate the hierarchical structure of linuxconf.
 | Please Note |
|---|---|
If you don't see the tree menu interface shown above, follow these instructions: |
Open Control => Control files and systems => Configure linuxconf modules
Select the treemenu check box
Click Accept
Click Quit
Restart linuxconf
When you use the tree menu view, finding the appropriate panel should be simple and fast. Collapse and expand sections by clicking on the + or - next to the menu item.
Selected entries will appear as tabs in the right-hand panel and will remain there until closed. If you end up with more tabs open than you like, just select Cancel on the bottom of each tab to close it without making any changes, or Accept to implement them.
Enabling Web-Based linuxconf Access
For security reasons, Web-based access to linuxconf is disabled by default. Before attempting to access linuxconf with a Web browser, you'll need to enable access. Here's how to do it:
Open Config => Networking => Misc => Linuxconf network access
In the Linuxconf html access control dialog box, enter the hostname of any computers that should be allowed access to Linuxconf. This includes your own system, if you wish to use the Web-based interface locally. Web accesses related to linuxconf may be logged to your system's htmlaccess.log file by selecting the check box.
Select the Accept button.
Web-based access should be enabled. To test it out, go to a system that you added to the access control list. Then, launch your Web browser, and enter the following URL:
http://<host>:98/ |
(Replace <host> with your system's hostname, of course. Also, remove the "disable=yes" line from the /etc/xinetd.d/linuxconf file and then run the command /sbin/service xinetd reload from a shell prompt.) You should see the main linuxconf page. Note that you will need to enter your system's root password to gain access beyond the first page.
You can also enable network-wide access to linuxconf by following the same steps, by entering a network name instead of a hostname.
Adding a User Account
Adding a user is one of the most basic tasks you will encounter in administering your system. To add a user:
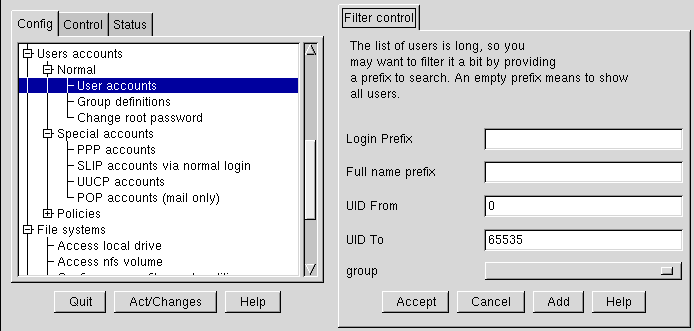
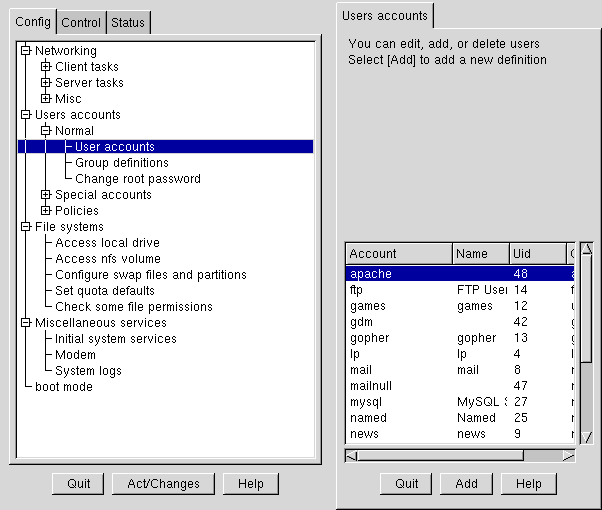
Open Config => Users accounts => Normal => User accounts. Linuxconf may show you a filter screen (see Figure 3-2).
You can use the filter screen to select a smaller range of accounts than the full list. To get the full list, select Accept without changing any of the parameters. For detailed information on the various filters, select the Help button on the Filter control screen. Once you've applied or bypassed the filter, you'll see the Users accounts tab (see Figure 3-4).
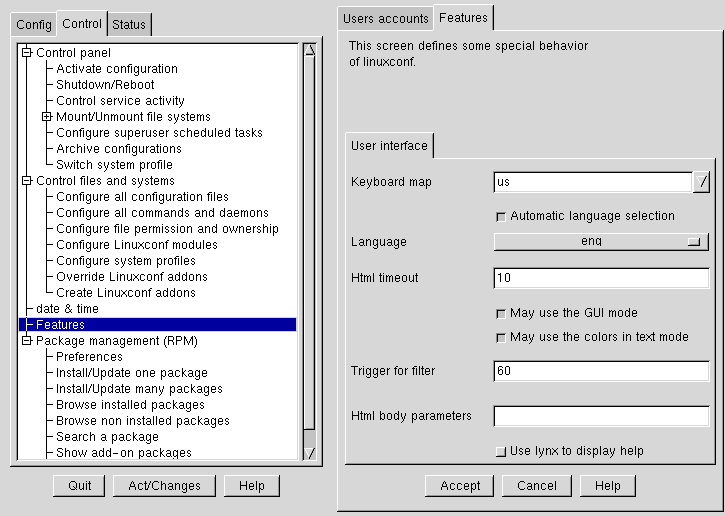
(You can control the filter using Control => Features. You'll see the Features tab, which allows you to set the Trigger for filter parameter, as shown in Figure 3-3.
The Trigger for filter field sets the number of entries that will pop up a filter screen.)
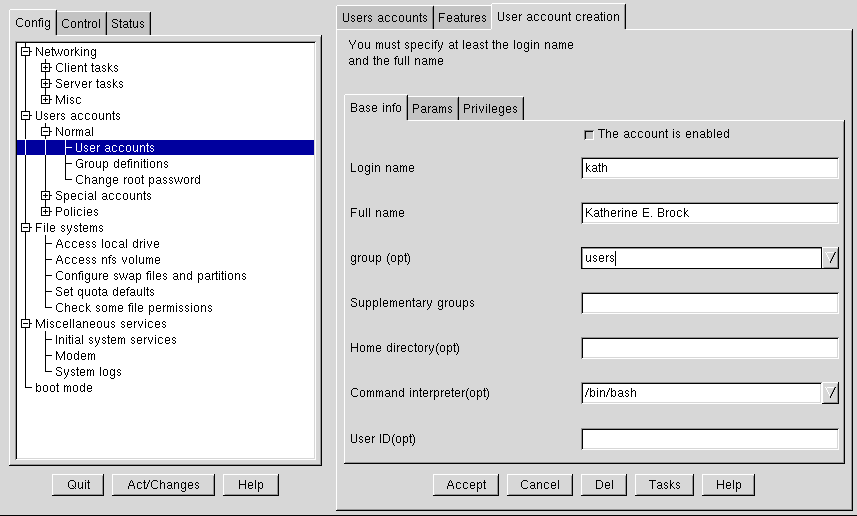
Select Add. This will open the User account creation tab (see Figure 3-5).
The User account creation screen includes the Base info, Params and Privileges sections. Only the Login name is required, but you should be aware of the other fields, which you may or may not want to fill in.
Base info for User Accounts
The Login name is the name of the account and is usually all lowercase letters. First or last names, initials or some combination thereof are fairly common login names. For a user named John T. Smith, smith, john, jts, or jsmith would be common user names. Of course spike or something else works just fine, too. You can also use numbers, so jts2 would be fine if you had a second person with the same initials. There is no default for this field.
The Full name is the name of the user or the account. For an individual, it would be their name, John T. Smith for example. If the account represents a position rather than a person, the full name might be the title. So an account called webmaster might have a full name of Red Hat Webmaster or just Webmaster. There is no default for this field.
Since Red Hat Linux uses the User Private Group scheme, each user will be assigned to a default group consisting only of the user. For more information on User Private Groups, see the section called User Private Groups in Chapter 2.
In the Supplementary groups field, you can specify additional groups. Group names should be separated by spaces. The default for this field is blank, meaning no supplementary groups are specified.
The Home directory specifies the home or login directory for the account. The default is /home/login, where login is replaced by the login name. A home directory is your starting point in the directory structure when you log in, or if in X, for each Xterm window opened. This is also where account specific preference files are stored.
The Command interpreter is the default shell for the account. The bash shell is the default shell for Red Hat Linux.
The User ID (UID) is the number associated with each user account. This is automatically generated by the system when the account is created, so just leave this field blank. The system uses the UID to identify an account.
Params for User Accounts
The Params are used for password and account management. By default, all of the settings are Ignored, so they are unused. Must keep # days sets a minimum number of days for a user's password.
The Must change after # days field can be set to make a user's password expire after a certain number of days. If you want to warn them that the password is going to expire (a good idea), the Warn # days before expiration field should be used.
If you'd like to have their account set to expire after a certain number of days, use the Account expire after # days field. You could alternatively set a hard Expiration date.
Privileges for User Accounts
In the Privileges section, you can grant access and/or control over various aspects of system configuration. As a default, regular users are denied all privileges on this screen. You may instead choose to grant or to silently grant them specific privileges. The difference between Granted and Granted/silent is that if the privilege is granted, linuxconf will ask for the user's password before allowing them the privilege. If the privilege is granted silently, linuxconf will not prompt for their password.
Generally, careful system administrators won't grant users any system configuration privileges unless it is absolutely necessary. If you do grant privileges, be careful when granting them silently. If a user with silently granted privileges logs in to his/her machine and walks away, their privileges are wide open for the next person who sits down at their desk. Silently granted privileges are less risky if used on machines in a physically restricted area.
May use linuxconf: the user is allowed to access all of linuxconf's capabilities, and they can set up or change linuxconf parameters. Note that use of linuxconf is separate from the privilege of activating configuration changes. System administrators might want to grant the use of linuxconf, but deny the activation privilege, so that the sysadmin has a final "yes/no" on whether to activate any configuration changes.
May activate config changes: After you change a parameter in linuxconf, at some point you'll have to indicate to linuxconf that the changes you made should be applied. Depending upon the flavor of linuxconf that you're using, you might do this by clicking on an Activate the changes button in GUI linuxconf, or clicking on an Accept button in Web-based linuxconf, or selecting an Accept button in text-mode linuxconf, etc.
You can grant the privilege of activating changes to a user. In that case, the user will be able to activate any changed system configuration parameters in linuxconf.
May shutdown: A user can be granted the right to shutdown the system. Note that Red Hat Linux is set in /etc/inittab to cleanly shutdown following the Ctrl-Alt-Del keystroke combination.
You can also grant the user the privileges to switch network modes, to view system logs, and even give someone superuser equivalence.
Once you have entered the login name and any other desired information select the Accept button at the bottom of the screen. If you decide against creating a new user, select Cancel instead.
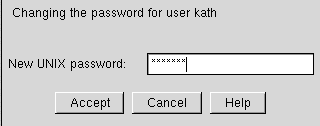
When you click on Accept linuxconf will prompt you to enter the password, as in Figure 3-6. You'll have to re-type the password, to prevent unusable passwords caused by typos. Passwords must be at least six characters in length, but you can increase the required length and set other parameters for users' passwords at the Users Accounts => Policies => Password & Account Policies screen.
Good passwords contain a combination of letters, numbers, and special characters. It should use both upper case and lower case letters. Don't use your username, your anniversary, your social security number, your dog's name, your middle name or the word root. Don't use any variation of a word associated with your account or with yourself. Don't use a word that can be found in a dictionary; dictionary words are easy to crack.
A simple technique for creating a password is to use the first letters from each word of a phrase that is familiar to you (a line from a favorite song might be appropriate). Make a few letters uppercase, and insert a few numbers and/or special characters in place of letters and you'll have a decent password.
Press the Accept button again when finished. The system will let you know if it thinks the password is easy to crack; if you get a warning message, don't use the password.
Modifying a User Account
Go to Config => Users accounts => Normal => User accounts, use the filter if necessary, and then select the account that you wish to modify.
See the section called Adding a User Account if you need guidance for how to fill in the user accounts fields.
To implement the changes select Accept. If you decide against making any changes select Cancel. This guarantees that no changes are made.
Changing a User's Password
Open Config => Users accounts => Normal => User accounts. This will open the Users accounts tab (see Figure 3-4).
You may see a filter screen, depending upon the settings you've provided on the Control => Features screen. If you want the full list, select Accept without changing any of the parameters. For detailed information on the various filters, select the Help button on the Filter control screen.
Select the account whose password you wish to change. This will open the User information screen.
Select Passwd from the options at the bottom of the screen.
Linuxconf will prompt you to enter the new password. There is also a field called Confirmation where you will need to type the password again. This is to prevent you from mistyping the password. See the section called Adding a User Account for guidance on choosing a password. If you decide against changing the password, select Cancel. Once you have entered the new password select Accept.
Changing the Root Password
Because of the security implications of root access, linuxconf requires you to verify that you currently have access to the root account.
Open Config => Users accounts => Normal => Change root password.
You'll first need to enter the current root password to verify access to the root account.
Once you have entered root's current password, it will prompt you for a new password. In the Confirmation field, type the password again. This is to prevent you from mistyping the password. See the section called Adding a User Account if you need guidance on choosing a password. Be sure to choose a good password! If you decide against changing the root password, just select Cancel. Once you have entered the new password select Accept.
Disabling a User Account
Disabling a user's account is preferable to deleting a user's account, unless you need the storage space or you're certain that his/her data will not be needed in the future. If a user's account is disabled, they will not be allowed to log in.
Open Config => Users accounts => Normal => User accounts.
Select an account.
De-select the check-box that states that The account is enabled. Select the Accept button at the bottom of the window and you're all set.
The account is disabled and can be enabled later using a similar method.
Enabling a User Account
By default, all newly created user accounts are enabled. If you need to enable an account, you can use linuxconf to do it.
Open Config => Users accounts => Normal => User accounts. Select an account. Select the The account is enabled checkbox.
Deleting a User Account
 | Please Note |
|---|---|
While there are options for retaining files associated with an account, any files that are deleted are gone and effectively unrecoverable. Take care when using this option! |
To delete an account:
Open Config => Users accounts => Normal => User accounts.
On the User accounts screen (see Figure 3-4) select the account you wish to delete.
At the bottom of the User information screen, select Del to delete the account.
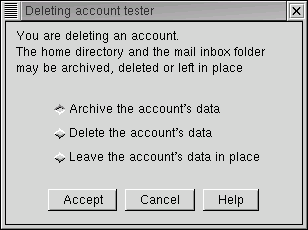
Linuxconf will then prompt you with a list of options.
The default option is to archive the account's data. The archive option has the following effects:
Removes the user from the user accounts list;
Takes everything contained in the user's home directory and archives it (using tar and gzip compression), storing the resulting file in the /default_home_directory/oldaccounts directory. For an account named useraccount the filename would be similar to:
useraccount-2000-01-10-497.tar.gz
The date indicates when the account was deleted, and the number following it is the ID of the process that actually performed the deletion. The oldaccounts directory is created in the same place as all of your user directories, and is created automatically the first time you remove a user account using this option.
Files not contained in the user's home directory, but owned by that user remain. The file is owned by the deleted account's user ID (UID). If you create a new account and specifically assign it the UID of a deleted account, it will then become the owner of any remaining files.
Selecting Delete the account's data on the Deleting account <accountname> screen (see Figure 3-7) will:
Remove the user from the user accounts list;
Remove the user's home directory and all its contents.
 | Please Note |
|---|---|
Files not contained in the user's home directory, but owned by that user will remain on the system. The file will still be owned by the deleted account's user ID (UID). If you create a new account and specifically assign it the UID of a deleted account, it will then become the owner of any such "orphaned" files. |
Selecting Leave the account's data in place on the Deleting account <accountname> screen (see Figure 3-7) will:
Remove the user from the user accounts list;
Leave the user's home directory (with all its files) in place.
 | Please Note |
|---|---|
Files and directories owned by the deleted account's user ID (UID) will remain on the system. If you create a new account and specifically assign it the UID of a deleted account, it will then become the owner of these "orphaned" files. |
Groups
All users belong to one or more groups. Just as each file has a specific owner, each file belongs to a particular group as well. The group might be specific to the owner of the file, or may be a group shared by all users. The ability to read, write or execute a file can be assigned to a group; this is separate from the owner's rights. For example, the owner of a file will be able to write to a document, while other group members may only be able to read it.
Creating a Group
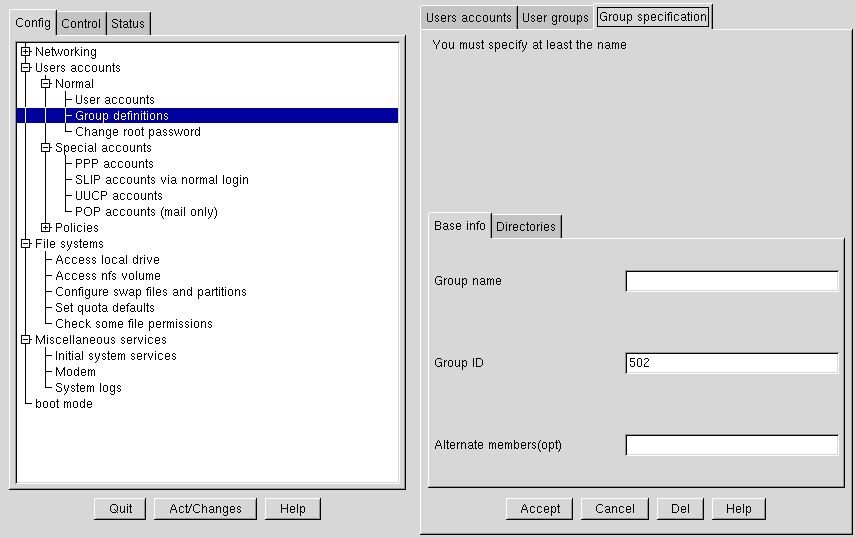
To create a new group:
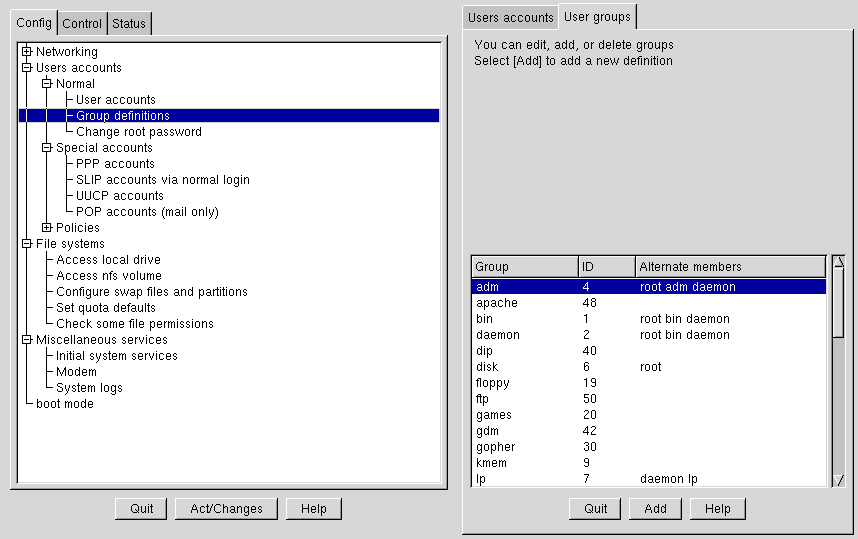
Open Config => Users accounts => Normal => Group definition.
You may see a filter screen, depending upon the settings in Control => Filters. Either provide a filter, or select Accept to bypass the filter.
Select Add at the bottom of the User groups screen.
Enter a group name. You may also wish to specify members of the group and can do so in the Alternate members field. The list of users should be space delimited, meaning that each username must have a space between it and the next one. Leave the Group name field blank, so that the system will assign a Group ID (GID) to your new group. When you're finished, select Accept and the group will be created.
Deleting a Group
To delete a group:
Open Config => Users accounts => Normal => Group definitions.
You may see a filter screen, depending upon the filter setting in Control => Features. You can use the filter to narrow your choice of groups by specifying a prefix.
With or without a prefix select Accept at the bottom of the screen.
On the User groups screen (see Figure 3-8) select the group you wish to delete.
You'll be presented with the Group specification screen (see Figure 3-9).
Select Del to delete the group. Linuxconf will then prompt you to confirm the deletion. Choose yes to delete the group.
The group's files will still remain and their respective owners will still have sole control over them. The group name will be replaced with the deleted group's ID. The files may be assigned to a new group by using the chgrp command. More information on chgrp can be found by typing the command info chgrp or man chgrp at the shell prompt. If a new group is created and the deleted group's ID is specified then the new group will have access to the deleted group's files. Don't worry, linuxconf doesn't recycle old group numbers any more than it does old user IDs, so it won't happen by accident.
Modifying Group Membership
There are two ways to modify the list of users that belong to a group. You can either update each user account itself, or you can update the group definitions. In general, the fastest way is to update each of the group definitions. If you're planning on changing more information for each user than just the group information, then updating each user account may prove easier.
We'll start by detailing the group definitions method.
Start linuxconf by typing linuxconf at the shell prompt.
Open Config => Users accounts => Normal => Group definitions.
Depending on the filter settings in Control => Features, you may see a filter screen. Use the filter to narrow the list, or just select Accept to bypass the filter.
Select the group you wish to modify. This will open the Group specification screen (see Figure 3-9).
Add or remove each user from the Alternate members field. Make sure that all of the user names are separated by a space character.
Select Accept, which can be found at the bottom of the screen.
This will automatically update each user account with the group showing up in the Supplementary groups field if added or absent if removed.
Adding and removing groups can also be done by modifying each individual user account.
Start linuxconf by typing linuxconf at the shell prompt.
Open Config => Users accounts => Normal => User accounts.
You may see a filter screen, depending on the settings in Control => Features. Use the filter to narrow the list or select Accept to bypass the filter.
On the User accounts screen (see Figure 3-4), select a user that you wish to update. You will be presented with the User information screen.
Add or remove the desired groups from the Supplementary groups field. Each group should be separated by a space character.
Once you've made all the changes you'd like, select Accept at the bottom of the screen.
This will automatically update the group definitions. Repeat the process for each user.
Filesystems
A filesystem is composed of files and directories, all starting from a single root directory. The root directory may contain any number of files and other directories, with each directory in turn following suit. The average filesystem often looks like an inverted tree with the directories as branches and the files as leaves. Filesystems reside on mass storage devices such as diskette drives, hard drives, and CD-ROMs.
For example, a diskette drive on DOS and Windows machines is typically referenced by A:\. This describes both the device (A:), and the root directory on that device (\). The primary hard drive on the same systems is typically referred to as the "C" drive because the device specification for the first hard drive is C:. To specify the root directory on the C drive, you would use C:\.
Under this arrangement, there are two filesystems — the one on A:, and the one on C:. In order to specify any file on a DOS/Windows filesystem, you must either explicitly specify the device on which the file resides, or it must be on the system's default drive (which is where DOS' C prompt comes from — that's the default drive in a system with a single hard drive).
Under Linux, it is possible to link the filesystems on several mass storage devices together into a single, larger, filesystem. This is done by placing one device's filesystem "under" a directory on another device's filesystem. So while the root directory of a diskette drive on a DOS machine may be referred to as A:\, the same drive on a Linux system may be accessible as /mnt/floppy.
The process of merging filesystems in this way is known as mounting. When a device is mounted, it is then accessible to the system's users. The directory "under" which a mounted device's filesystem becomes accessible is known as the mount point. In the previous paragraph's example, /mnt/floppy was the diskette drive's mount point. Note that there are no restrictions (other than common conventions) as to the naming of mount points. We could have just as easily mounted the floppy to /long/path/to/the/floppy/drive.
One thing to keep in mind is that all of a device's files and directories are relative to its mount point. Consider the following example:
A Linux System:
/ — system root directory
/foo — mount point for the CD-ROM
A CD-ROM:
/ — CD-ROM's root directory
/images — A directory of images on the CD-ROM
/images/old — A directory of old images
So, if the above describes the individual filesystems, and you mount the CD-ROM at /foo, the new operating system directory structure would be:
A Linux System (with the CD-ROM mounted):
/ — System root directory
/foo — CD-ROM root directory
/foo/images — A directory of images on the CD-ROM
/foo/images/old — A directory of old images
To mount a filesystem make sure to be logged in as root, or become root using the su command. For the latter, type su at the shell prompt and then enter the root password. Once you are root, type mount followed by the device and then the mount point. For example, to mount the first diskette drive on /mnt/floppy, you would type the command mount /dev/fd0 /mnt/floppy.
At installation, Red Hat Linux will create /etc/fstab. This file contains information on devices and associated mount points. The advantage to this file is that it allows you to shorten your mount commands and it controls which filesystems are automatically mounted when the system is booted.
Using the information in /etc/fstab, you can type mount and then either the mount point or the device. The mount command will look for the rest of the information in /etc/fstab. It's possible to modify this file by hand, or by using linuxconf.
Reviewing Your Current Filesystem
We'll start by looking at your current directory structure.
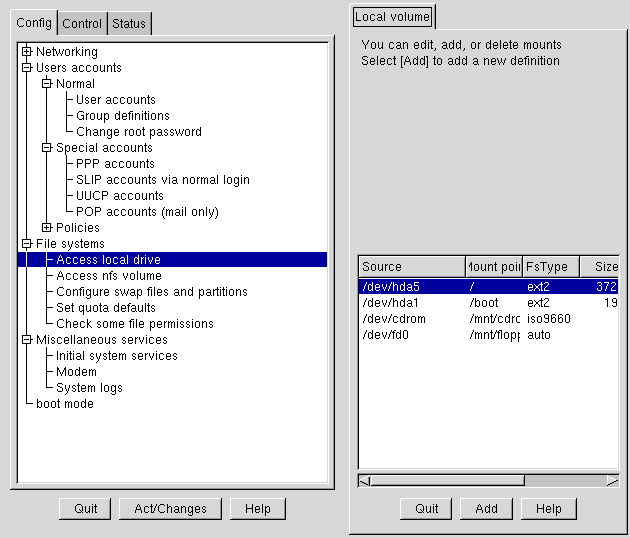
Open Config => File systems => Access local drive.
The fields, as shown in Figure 3-10, are:
Source: The physical hardware; hd indicates an IDE hard drive, fd indicates a diskette drive, and cdrom typically indicates a CD-ROM drive. If your system has a SCSI drive, you will see an sd instead. More than one drive of a type are listed by letters, so hda represents the first IDE drive, while hdb would be the second. In some cases, you'll see numbers following these letters; on hard drives, the numbers represent the partitions on that drive, while for diskette drives, this number refers to the actual unit.
Mount point: This is where in the system the drive is accessible from when mounted.
FsType: The type of filesystem. A standard Linux partition uses the ext2 filesystem type. A filesystem type of vfat indicates a DOS filesystem with long filename support, while a fat filesystem type is for DOS filesystems supporting traditional 8.3 filenames. The iso9660 filesystem type indicates a CD-ROM drive.

Please Note Red Hat Linux 7.0 can access FAT32 filesystems using the vfat filesystem type.
Size: Size may indicate the size of the filesystem in megabytes (M), or it may not be filled in.
Partition type: A description of the filesystem used on that partition (may not be filled in).
Status: Whether the device is mounted or not.
Filesystems from other machines on a network may also be available. These can range from single small directories to entire volumes. No information on Size or Partition type is available for these partitions, either. Additional information on NFS filesystems (should you have any available) will be contained under:
Config => File systems => Access nfs volume
The screen is similar to the Local Volume screen (see Figure 3-10, with some notable differences in the information provided for each entry:
Source: This will be the name of the machine serving the filesystem, followed by the remote directory. For example: foo:/var/spool/mail where foo is the machine serving the directory, and /var/spool/mail is the directory being served.
FsType — This will always be "nfs."
Adding NFS Mounts
NFS (Network File System) is a way for computers to share sections of their local filesystem across a network. These sections may be as small as a single directory, or include thousands of files in a vast hierarchy of directories. For example, many companies will have a single mail server with individuals' mail files served as an NFS mount to each users' local systems.
To add an NFS mount:
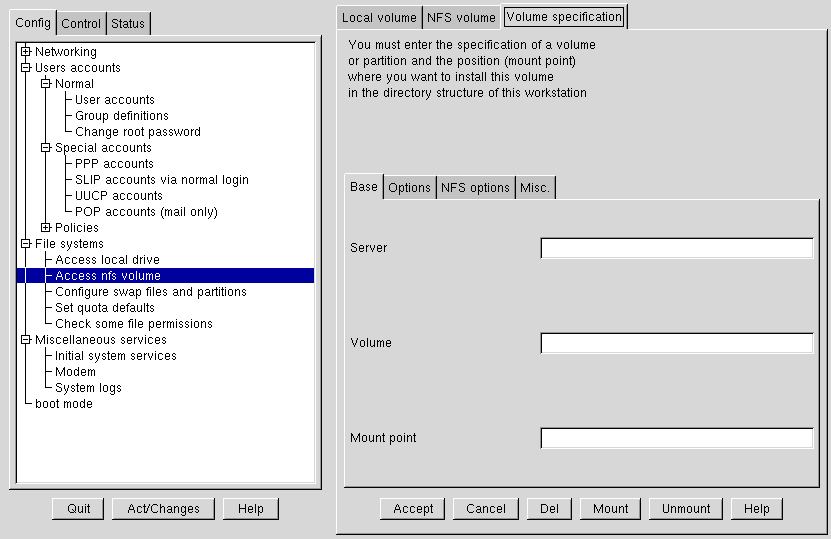
Open Config => File systems => Access nfs volume.
On the NFS volume screen, select Add.
The three fields on the Base tab are what you'll need to concern yourself with next (see Figure 3-11).
Server: The host name of the machine the desired filesystem resides on. For example, foo.bar.com.
Volume: The filesystem you wish to add. For example, /var/spool/mail.
Mount point: Where in your system you want the remote file system accessible from. For example, /mnt/mail.
This is all you need to get the mount created. Linuxconf will update your /etc/fstab file accordingly. If you are aware of additional requirements, please read the help file on the Volume specification screen and see the mount man page for more information.
Once you have entered the information, select Accept.
Getting Connected with Linuxconf (Network Configuration)
The first thing to determine when getting hooked up is whether you're connecting to a local area network, such as a group of computers in an office, or a wide area network, such as the Internet. Before continuing, it's important to know what hardware you have and how you intend to connect. If you're going to dial into another computer, then make sure your modem is installed and that the cables are arranged properly. If you're using a network card, make sure it is installed properly and that the cables are correctly connected. Regardless of what network configuration you specify, if every phone line or cable is not in place, you'll never get connected.
Network Connections
Setting up a network connection over Ethernet requires an entirely different type of setup. Network connections to Token Ring or ARCnet networks follow a similar procedure, but will not be discussed here.
First you will need to have an Ethernet card installed.
Start linuxconf by typing linuxconf at the shell prompt.
Open Config => Networking => Client tasks => Basic host information. The Host name tab will request a host name, which should be specified by default unless you did not setup your networking during the installation process. If it is not already specified, please take the time now to configure it. It should be specified as localhost.localdomain. Skip this tab. Select the tab for Adaptor 1.
The first item on this screen is a check box to indicate whether this adaptor is enabled or not. It should be checked if this is the one you intend to use. Below that is a choice of Config modes. Manual means that you will be providing all the information and entering it yourself. Dhcp and Bootp mean that your machine will be getting its network configuration information from a remote DHCP or BOOTP server. If you're not sure what option to choose, talk to your network administrator.
Required fields for DHCP or BOOTP:
Net device — The type of network card you are using; for example, eth0 would be the appropriate entry to use the first Ethernet card.
Kernel module — The correct module based on your network card; for further information see the list below.
For DHCP and bootp configurations you only need to specify the Net device and the Kernel module. For the Net device, you will choose from a list where the eth prefix represents Ethernet cards, arc specifies an ARCnet card and tr specifies Token Ring cards. A complete list of network cards and their respective modules can be found in Appendix A. For the most up-to-date list, please see our website at:
http://www.redhat.com/support/hardware |
The netmask information may be set by default, although depending on what kind of network you are setting up, or becoming a part of, you may need to specify this. If you are connecting to an ISP, ask them for the information. Most likely it will be 255.255.255.0.
Required fields for manual configuration:
Primary name + domain — The primary name is the name of your computer, while the domain is how your network is specified. For example, foo.bar.com; foo is the primary name and bar.com is the domain.
IP address — The address of the machine and will follow the pattern of x.x .x.x. For example, 192.168.0.13.
Net device — The type of network card you are using; eth0 would be the appropriate entry to use the first Ethernet card.
Kernel module — The correct module based on your network card.
Information on net devices and kernel modules is described above. The appropriate primary name + domain and IP address will depend on whether you are adding the computer to an existing network or creating a new network. For connecting to an existing network, contact your network administrator for the information. Getting a network connected to the Internet is beyond the scope of this book, and we recommend the following starting point:
TCP/IP Network Administration, 2nd Edition, by Craig Hunt (O'Reilly and Associates).
If you're setting up a private network that won't ever be connected to the Internet, then you can choose any primary name + domain name you would like and have several choices for IP addresses (See Table 3-1).
Table 3-1. Addresses and Examples
| Addresses available | Examples |
|---|---|
| 10.0.0.0 - 10.255.255.255 | 10.5.12.14 |
| 172.16.0.0 - 172.31.255.255 | 172.16.9.1, 172.28.2.5 |
| 192.168.0.0 - 192.168.255.25 | 192.168.0.13 |
The three sets of numbers above correspond to class a, b, and c networks respectively. The classes are used to describe the number of IP addresses available as well as the range of numbers. The numbers above have been set aside for private networks.
 | Please Note |
|---|---|
You should not use these IP addresses if you connect to the Internet since 192.168.0.* and 192.168.255.* are not reliably considered private. If you want your network to be connected to the Internet, or think you might want to at some point in the future, do yourself a favor and get yourself non-private addresses now. |
Name Server Specification
A name server and default domain are also needed to establish a network connection. The name server is used to translate host names such as private.network.com to their corresponding IP address such as 192.168.7.3.
The default domain tells the computer where to look if a fully qualified hostname isn't specified. Fully qualified means that the full address is given, so foo.redhat.com is the fully qualified hostname, while the hostname is simply foo. If you specified your default domain as redhat.com, then you could use just the hostname to connect successfully. For example ftp foo would be sufficient if your search domain is redhat.com, while ftp foo.redhat.com would be required if it wasn't.
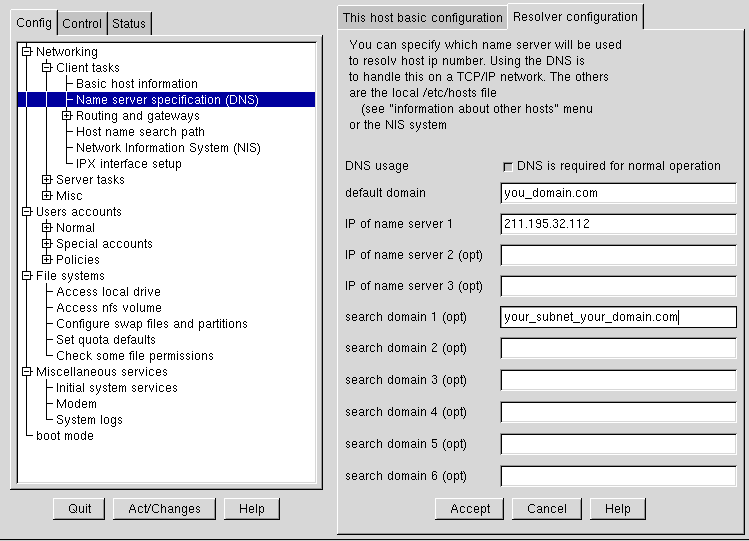
To specify the nameserver, open Config => Networking => Client tasks => Name server specification (DNS).
Nameservers are ranked according to the order in which they are accessed, so it's not unusual to see nameservers referred to as primary, secondary, tertiary and so on down the list if more than one is specified. Each of these must be an IP address and not a name, since the computer has no way to resolve the name until it connects to a nameserver.
In addition to a default domain, you can also specify search domains. Search domains work differently; they progress from one to six in a similar manner to the nameserver. However, they all take precedence over the default domain! Keep this in mind when specifying search domains. Search domains are not commonly used.
The one item not yet covered is the check box for DNS usage. If you are running a small private network with no Internet connection, then using /etc/hosts files and keeping them all synchronized will work. As you add more and more machines, the complexity increases until it is easier to have a single machine run a DNS than to continue to sync /etc/hosts files.
Another reason for not using DNS is if your network is going to use NIS instead. Note that NIS can be used in conjunction with DNS. So to sum it all up, unless you know why using /etc/hosts or NIS would be best for your situation, DNS is probably going to be your best choice.
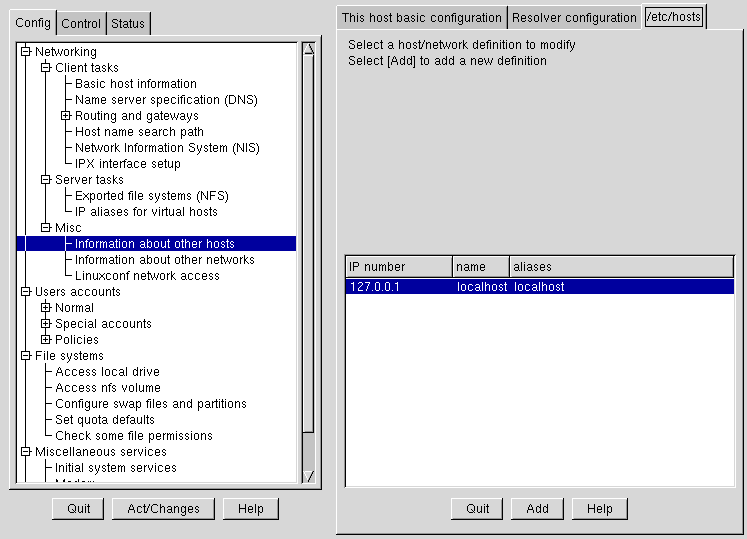
You can add, modify, or delete entries from the /etc/hosts file using linuxconf. Open Config => Networking => Misc => Information about other hosts.
To modify or delete an entry select it. To delete the entry, select Del at the bottom of the host/network definition screen.
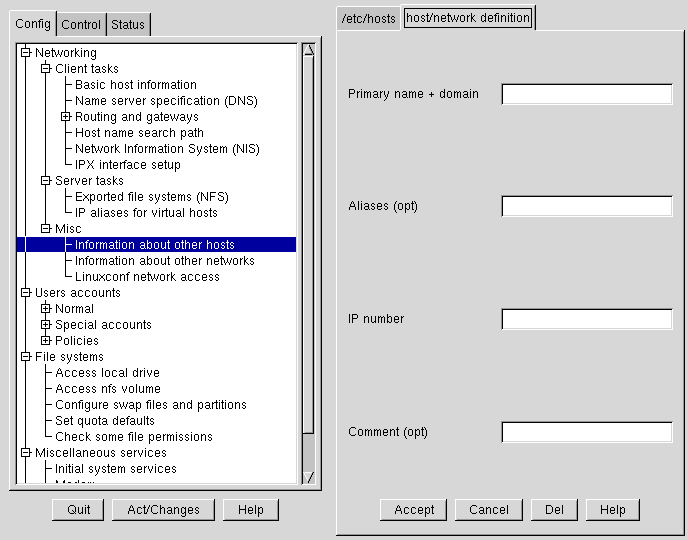
To modify it, change the information as necessary. To add a new entry, select Add at the bottom of the /etc/hosts screen. This will also open the host/network definition screen.
Required Fields:
Primary name + domain — The primary name is the name of the computer, while the domain is how the network it is attached to is specified. For example, given foo.bar.com, foo is the primary name and bar.com is the domain.
IP number — Also referred to as IP address; this is the address of the machine and will follow the pattern of x.x. x.x. For example, 192.168.0.13.
Optional Fields:
Aliases — A shorthand for the fully qualified domain name. This is often the same as the primary name. So, for example, if the fully qualified domain name is foo.bar.com, you could select foo as the alias.
Comment — A comment on the machine. For example, "The remote nameserver."
Once finished, select Accept.
Finding Your Way Through linuxconf
This table provides a quick reference for this chapter. Unfortunately, it doesn't provide a complete quick reference for linuxconf, which has many more capabilities than this documentation provides.
Table 3-2. Linuxconf Quick Reference
| What do you want to do? | Where to find it in linuxconf |
|---|---|
| Add/modify/disable/delete a user account | Config => Users accounts => Normal => User accounts |
| Change a user's password | Config => Users accounts => Normal => User accounts |
| Change the root password | Config => Users accounts => Normal => Change root password |
| Configure networking | Config => Networking => Client tasks => Basic host information |
| Create/delete a group | Config => Users accounts => Normal => Group definitions |
| Edit parameters for passwords | Users Accounts => Password & Account Policies |
| Disable tree menu | Control => Control files and systems => Configure linuxconf modules |
| Enable Web-based access to linuxconf | Config => Networking => Misc => Linuxconf network access |
| Modify /etc/hosts | Config => Networking => Misc => Information about other hosts |
| Modify group membership | Config => Users accounts => Normal => Group definitions or Config => Users accounts => Normal => User accounts |
| Set filter parameters | Control => Features |
| Specify a nameserver (DNS) | Config => Networking => Client tasks => Name server specification (DNS) |
| View filesystem | Config => File systems => Access local drive or Config => File systems => Access nfs volume |